Tips
Forget the images of sentient robots taking over. While Artificial General Intelligence (AGI) captures headlines, the real AI revolution isn’t a distant thunderclap; it’s a subtle, pervasive current already reshaping the landscape of our daily lives and the bedrock of our businesses. It’s less about replacement and more about refinement, augmentation, and sometimes, unintentional redirection.
So, how is this “quiet AI” affecting you and your business in ways you might not even realize?

Docker, Free Tools
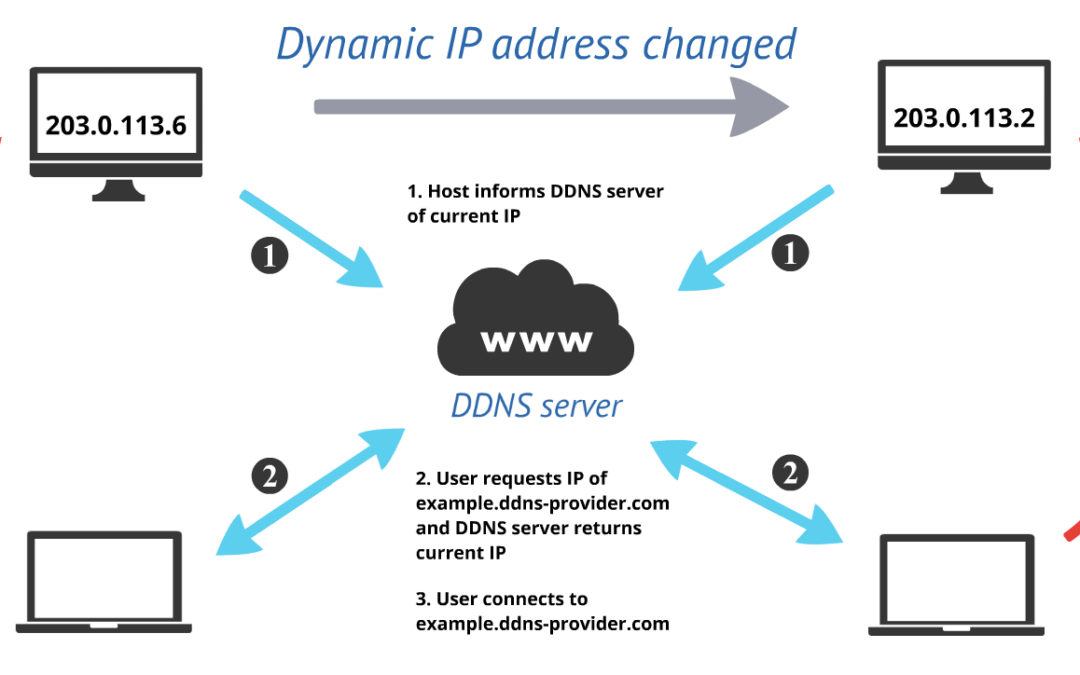
We recently started self hosting our own DDNS service. You can check it out at https://ddns.bcsddns.com. Once you submit your hostname, be sure to save the curl command that’s generated, you will need it to update your hostname.This service will assign a...

Tips
Here are some best practices for creating and managing passwords.

Tips
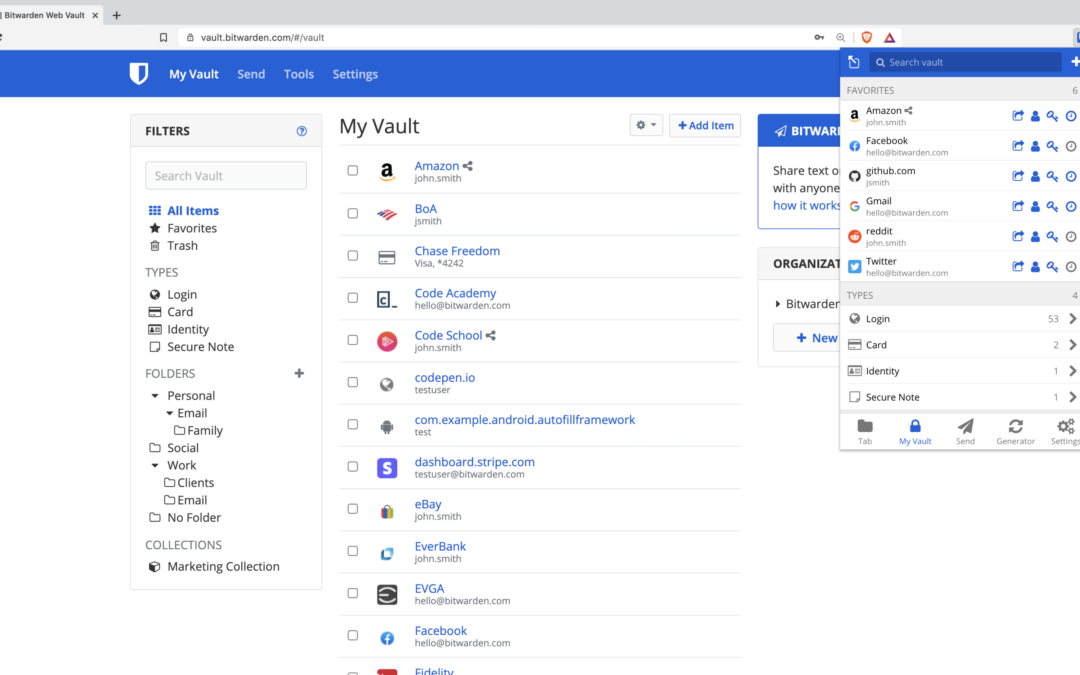
Password managers are tools that help you generate and store strong, unique passwords for all of your online accounts. They can be very useful for helping you to keep track of your passwords and increasing the security of your accounts. Pros of password managers: They...

Docker, Tips
OpenAI’s Whisper Audio to text transcription right into your web browser! Visit the Github Repo for more information Features Record and transcribe audio right from your browser. Upload any media file (video, audio) in any format and transcribe it. Download .srt...

Tips
docker-compose.ymlversion: "2.1" services: nb_app: image: lscr.io/linuxserver/netbox:latest container_name: netbox environment: - PUID=1000 - PGID=1000 - TZ=${TZ} - SUPERUSER_EMAIL=${SUPERUSER_EMAIL} - SUPERUSER_PASSWORD=${SUPERUSER_PASSWORD} -...

Tips
With a surge in the popularity of SSDs (solid state drives), one of the most basic questions on the mind of new buyers is: Why should I go for an SSD upgrade?

Tips
Sweeping the Globe both in homes and businesses, this hot new technology essentially “extends” the signal of your wireless router to provide you with reliable wireless Internet access anywhere in your office or home.

Tips
The history of the computer inevitably includes the development of electronics, we look at the explosive growth of electronics in the late 1930s and early 1940s.

Tips
In ‘History of the Computer – the emergence of Electronics’, we saw how the development of Radar during the second world war led to an understanding of pulse technology. At the same time methods were refined for the calculations required for the ballistic trajectories. From these beginnings, the digital computer was developed.

Tips
Understanding how fiber optics are made and function for uses in everyday life is an intriguing work of art combined with science. Fiber optics has been fabricated from materials that transmit light and are made from a bundle of very thin glass or plastic fibers enclosed in a tube. One end is at a source of light and the other end is a camera lens, used to channel light and images around the bends and corners. Fiber optics have a highly transparent core of glass or plastic…

Tips
Many business managers and owners discount the idea of installing a CCTV system on their premises. Worried about costs and benefits, they use other security measures to protect their stock and their staff.
CCTV systems could be more beneficial than you think. Here are three key ways that CCTV can help to protect your business.
Deterrent
Although they won’t stop all crime, it is thought that visible CCTV systems act as a deterrent to would-be criminals. It’s far less

Tips
I have a few customers that use basic IMAP e-mail hosting through a hosting provider such as Bluehost. This basic email account provides all the features they need but they were getting blasted with hundreds of spam messages every day. Most of our customers are using Exchange Online and G-Suite, both of which filter spam very well. I was struggling to configure SpamAssassin to filter out the bad stuff without filtering out the good stuff and couldn’t really find any tutorials online to help with this matter. Here we go…

Tips
Wireless networking can be thought of as Morse code for computers.For all its complicated ability, is far simpler to use than you might expect.

Tips
A computer network is a collection of two or more computers with communication between them through a medium. The communication medium can be through radio waves, wires, infrared, optical fibers etc.
A computer network is an integral part of our daily lives, with the most important reason being that of communication. The use of computer networking is to share resources like fax machines, printers, modems, files etc., and its other uses are a database server, computer server, e…

Tips
No sane person would ever like someone else reading her email. Or for that matter some other person using her password and breaking into a financial institution. You should, therefore, choose a strong, secure password in such a manner that would be a hard nut to crack for others and easy for you to remember. The more random and mixed-up you make it, the harder it is for others to crack. Mind you, if your password is compromised, the password crackers will even take over your identity.

Tips
Router is a computer device that receives or forwards data packets to and from the Internet towards a destination in the process called routing. Router is the essential component of the computer networking that enables any sent data to arrive at the right destination.
As an illustration, imagine that the Internet is the world and one computer is one household. Other computers connected through the Internet are households around the world. Say one household will send a let…

Tips
When you use computers and the Internet in your business, it’s all too easy to start feeling like you’re drowning in a sea of nonsense. Computer-related things tend to have a language all their own, and while you don’t need to know all of it, there are many confusing words and phrases that you’re going to come across sooner or later. Here’s a quick primer.

Tips
If you are in the market for a computer, there are a number of factors to consider. Will it be used for your home, your office or perhaps even your home office combo?
Tips
While many small companies only call in a local computer consulting business when something computer-related breaks, there’s a lot to be gained by forging a proactive, long-term relationship with a local computer consulting business in your area.
Tips
An explanation of how attacks from other computers, called denial of service attacks, can ultimately shut down an entire network by overloading the routers that relay the information.

Tips
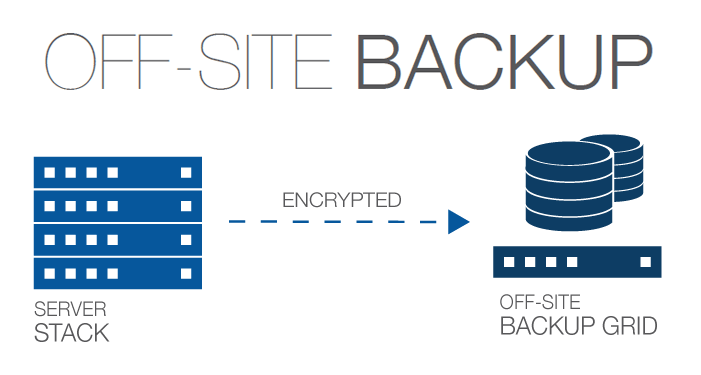
An informative article detailing the best practices of data backup
Tips
IP address (Internet Protocol address) is a unique address that certain electronic devices use in order to identify and communicate with each other on a computer network utilizing the Internet Protocol standard (IP)—in simpler terms, a computer address. Any...

Tips
An article about how to find wired and wireless network card MAC addresses. It also goes into details about the output of the “ipconfig /all” command and “arp” command

Tips
Software as a Service (SaaS) is a software delivery model in which a software application is hosted by a third-party provider and made available to customers over the internet. Customers can access the software through a web browser, rather than installing it on their...

Tips
Fiber optic internet is often considered to be superior to other types of internet connectivity because it is capable of providing very high speeds and a stable connection. This makes it suitable for activities that require a lot of bandwidth, such as streaming...

Tips
Android and iPhone are two of the most popular mobile operating systems. Both are used on a wide range of smartphones and other devices, and both have their own strengths and weaknesses. One of the main differences between Android and iPhone is the software and user...

Tips
A data center is a facility that organizations use to house their critical applications and data. It typically includes redundant or backup power supplies, redundant data communications connections, environmental controls (e.g., air conditioning, fire suppression),...

Tips
Open source refers to a type of software whose source code is available to the public, meaning anyone can access, modify, and distribute the software for free. This is in contrast to proprietary software, which is owned by a company or individual and is not freely...

Tips
Solid state drives (SSDs) are storage devices that use memory chips to store data. They are faster and more reliable than traditional hard disk drives (HDDs), which use spinning disks to access data. There are several types of SSDs available, including: SATA SSDs:...

Tips
One area that saw significant developments in 2021 was artificial intelligence (AI). AI technologies, such as machine learning and natural language processing, were being applied to a wide range of applications, including autonomous vehicles, personal assistants, and...

Tips
ChatGPT is a natural language processing (NLP) model developed by OpenAI. It is based on the GPT (Generative Pre-training Transformer) model, which is a transformer-based language model that has been trained on a very large dataset to generate human-like text. ChatGPT...

Tips
There are several steps you can take to help keep your family safe on the internet: Educate your family members about internet safety: Make sure that everyone in your family knows how to recognize and avoid potential online dangers, such as scams, phishing attacks,...

Tips
A Virtual Private Server (VPS) is a type of hosting service that allows an individual or organization to host a website or application on a virtual machine, which is a simulated computer environment. A VPS is like having a dedicated server, but it is actually a part...

Tips
Quantum computing has the potential to revolutionize many fields and change the world in significant ways. Here are a few examples of how quantum computing could impact various industries and areas of society: Healthcare: Quantum computers could be used to simulate...

Docker, Tips
docker-compose.ymlversion: "2.1" services: nb_app: image: lscr.io/linuxserver/netbox:latest container_name: netbox environment: - PUID=1000 - PGID=1000 - TZ=${TZ} - SUPERUSER_EMAIL=${SUPERUSER_EMAIL} - SUPERUSER_PASSWORD=${SUPERUSER_PASSWORD} -...

Tips
I have a need for speed… My self-hosted journey has been very informative in many ways and while along that journey I stumbled across Ghost. It’s open source and free to self-host, so I figured I would give it a shot. According to ghost.org: Ghost is a...

Tips
Computer backup is so important to your computer that to ignore it is to risk its damnation.